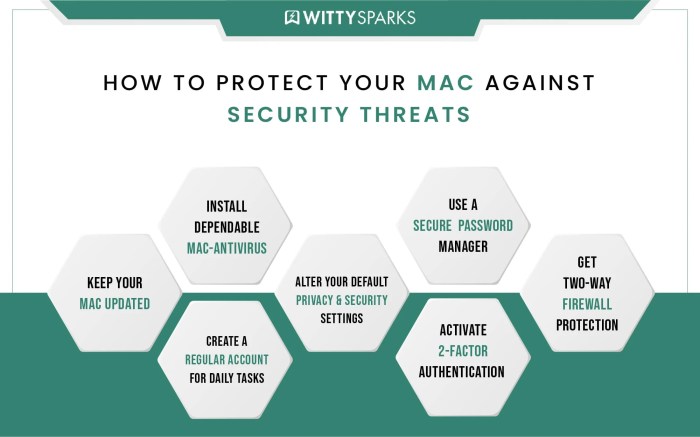
How To Harden Up Your Mac, Courtesy Of The Nsa
How To Harden Up Your Mac, Courtesy of the NSA, is a guide that takes you beyond the basics of Mac security. We’ll dive into the strategies the NSA uses to protect their systems, applying them to your everyday Mac.
This isn’t just about installing antivirus software; it’s about understanding the vulnerabilities, building a layered defense, and developing proactive habits to keep your data safe.
From understanding the fundamentals of macOS security to implementing advanced measures like sandboxing and firewalls, we’ll explore the steps you can take to make your Mac a fortress against cyber threats. Think of it as a security bootcamp, but instead of push-ups, we’ll be focusing on encryption, strong passwords, and the latest security best practices.
Understanding Mac Security Basics
macOS is built with a strong foundation of security features, but it’s essential to understand the fundamental principles behind them to protect your data and privacy. While Macs are generally considered more secure than other operating systems, they are not immune to vulnerabilities.
You know how the NSA recommends hardening up your Mac? Well, one way to do that is by taking control of your privacy settings. One easy step is to disable Facebook Places, which lets your friends know where you are.
You can learn how to disable Facebook Places here. It’s a small change, but it can make a big difference in protecting your privacy, which is a big part of hardening up your system.
Common Vulnerabilities in Mac Systems
Macs are not immune to security threats. Common vulnerabilities include:
- Malware:Like any other operating system, Macs can be infected with malware, which can steal your data, spy on your activities, or even take control of your computer. The majority of Mac malware is designed to steal financial information and personal data.
- Phishing Attacks:These attacks use deceptive emails, websites, or messages to trick users into revealing sensitive information like passwords or credit card numbers.
- Unpatched Software:Outdated software can contain vulnerabilities that attackers can exploit. Software updates often include security patches that fix these vulnerabilities.
- Weak Passwords:Using weak passwords makes it easier for attackers to guess your login credentials.
- Unsecured Wi-Fi Networks:Connecting to unsecured Wi-Fi networks can expose your data to eavesdropping.
Importance of Software Updates and Security Patches
Software updates are crucial for maintaining the security of your Mac. They often include security patches that fix vulnerabilities that attackers could exploit. These patches can address issues like:
- Fixing bugs:Software updates often include fixes for bugs that could be exploited by attackers.
- Improving security features:Updates can enhance existing security features or introduce new ones to better protect your data.
- Closing vulnerabilities:Software updates often close known vulnerabilities that could allow attackers to gain access to your system.
Securing Your Mac Against Malware
While Macs are generally considered more secure than Windows computers, they are not immune to malware. Malware is software designed to harm or disrupt a computer system. There are several types of malware that can affect Macs, and understanding them is crucial to protecting your device.
Types of Malware That Target Macs
Mac malware is becoming increasingly common, with attackers finding new ways to exploit vulnerabilities in macOS. Understanding the different types of malware helps you identify potential threats and take appropriate precautions.
- Viruses:These are programs that can replicate themselves and spread to other files on your computer. Viruses can cause a range of problems, including data loss, system crashes, and slow performance.
- Worms:These are self-replicating programs that can spread from one computer to another without any human interaction. Worms can spread through email attachments, file-sharing networks, or vulnerabilities in software.
- Trojan Horses:These are programs that appear harmless but actually contain malicious code. Trojan horses can steal your personal information, install other malware on your computer, or give attackers remote access to your system.
- Spyware:This type of malware secretly monitors your online activity and collects personal information without your knowledge or consent. Spyware can be used to steal your passwords, credit card numbers, and other sensitive data.
- Adware:This malware displays unwanted ads on your computer. Adware can be annoying and intrusive, and it can sometimes lead to other malware infections.
- Ransomware:This type of malware encrypts your files and demands payment to unlock them. Ransomware can be very destructive, and it can be difficult to recover your files if they are encrypted.
Protecting Your Data with Encryption
Encryption is a crucial part of protecting your data on a Mac, especially if you handle sensitive information. It essentially scrambles your data, making it unreadable without the correct key. This means that even if someone steals your Mac, they won’t be able to access your files.
FileVault Encryption, How To Harden Up Your Mac, Courtesy of the NSA
FileVault encryption is a built-in feature on macOS that encrypts your entire hard drive. It’s a powerful tool that adds an extra layer of security to your data. Here’s how to set up FileVault encryption:
- Go to System Preferences> Security & Privacy> FileVault.
- Click Turn On FileVault.
- Choose how you want to recover your encryption key:
- Save it to iCloud:This is the most convenient option, but it requires you to have an iCloud account and trust Apple’s security.
- Save it to a USB drive:This is a more secure option, but you need to keep the USB drive safe.
- Enter your Apple ID password and follow the onscreen instructions.
Once FileVault is enabled, your Mac will automatically encrypt your hard drive in the background. You’ll need to enter your password each time you start up your Mac.
Comparing Encryption Methods
macOS offers different encryption methods, each with its strengths and weaknesses:
- XTS-AES-128:This is the default encryption method used by FileVault. It’s a strong and widely used algorithm.
- AES-128:Another strong encryption algorithm that is less common than XTS-AES-128.
Choosing the right encryption method depends on your security needs. For most users, the default XTS-AES-128 is sufficient.
Managing User Accounts and Permissions: How To Harden Up Your Mac, Courtesy Of The NSA
Managing user accounts and permissions on your Mac is crucial for maintaining a secure system. It allows you to control access to sensitive data and prevent unauthorized modifications. By understanding different user account types, configuring permissions, and employing strong security measures, you can significantly enhance the security of your Mac.
You know how the NSA has all those cool tips on how to harden up your Mac? Well, they might not tell you this, but sometimes even the best security measures can be undone by a simple annoyance like auto-brightness.
If you’re like me, you find it super distracting, and you might want to check out How to switch off Auto Brightness in iOS 11 for some quick tips. Once you’ve got that sorted, you can go back to focusing on the NSA’s recommendations and keeping your Mac as secure as Fort Knox.
User Account Types and Permissions
User accounts on macOS come in different types, each with specific permissions and access levels. Understanding these types is essential for managing your system effectively.
| Account Type | Description | Permissions |
|---|---|---|
| Administrator | Has full control over the Mac, including installing software, managing users, and changing system settings. | Full access to all files and folders, ability to make changes to system settings. |
| Standard | Limited access to the Mac, cannot install software or make significant system changes. | Access to personal files and folders, limited access to system settings. |
| Guest | Temporary account with limited access, no ability to save data or make changes to the system. | Limited access to the system, cannot save data or make changes to system settings. |
Strong Passwords and Two-Factor Authentication
Using strong passwords and two-factor authentication is essential for protecting your Mac and its data. Strong passwords are complex and difficult to guess, while two-factor authentication adds an extra layer of security by requiring a second verification step, usually a code sent to your phone.
“A strong password is a combination of uppercase and lowercase letters, numbers, and symbols. Avoid using personal information like names or birthdays.”
“Two-factor authentication is a security measure that requires two forms of identification, such as a password and a code sent to your phone, to access an account.”
Configuring User Permissions
You can configure user permissions to restrict access to specific files, folders, and applications. This ensures that only authorized users can access sensitive data and prevents unauthorized modifications.
“You can use the ‘Sharing’ preferences pane in System Preferences to configure user permissions and access levels.”
“For sensitive data, consider creating separate user accounts with limited permissions and using file and folder permissions to restrict access.”
Securing Your Network Connection
Your Mac is only as secure as the network it’s connected to. Public Wi-Fi networks, often found in cafes, airports, and hotels, are particularly vulnerable to security risks. Understanding these risks and taking precautions is crucial for safeguarding your data and privacy.
Risks of Public Wi-Fi Networks
Public Wi-Fi networks can pose several security risks, including:
- Man-in-the-middle attacks:Hackers can intercept your internet traffic, potentially stealing your passwords, credit card information, or other sensitive data.
- Eavesdropping:Hackers can listen in on your online activity, including your browsing history, emails, and instant messages.
- Malware:Public Wi-Fi networks can be used to spread malware, which can infect your Mac and steal your data.
- Unsecured connections:Public Wi-Fi networks often lack strong encryption, making your data vulnerable to interception.
Setting Up a VPN Connection
A Virtual Private Network (VPN) creates a secure, encrypted tunnel between your Mac and the internet, protecting your data from prying eyes.
- Choose a reputable VPN provider:Research and select a VPN provider with a strong reputation for security and privacy.
- Download and install the VPN client:Most VPN providers offer dedicated apps for Mac.
- Create an account and subscribe to a plan:Most VPN providers offer free trials or limited free plans, but you’ll likely need a paid subscription for full functionality.
- Connect to a VPN server:Once you’ve installed the VPN client, select a server location and connect.
- Verify the connection:Ensure the VPN is active and working properly by checking the VPN client’s status or using a website like “What is my IP address?” to verify your IP address is from the chosen VPN server location.
Creating a Secure Home Network
A secure home network is essential for protecting your Mac and other devices from unauthorized access.
- Use a strong password for your router:Avoid default passwords and choose a complex password that includes a mix of uppercase and lowercase letters, numbers, and symbols.
- Enable WPA2 or WPA3 encryption:These protocols encrypt your network traffic, making it harder for hackers to intercept.
- Disable SSID broadcast:This prevents your network name from being visible to nearby devices, making it harder for hackers to find your network.
- Update your router’s firmware:Regular firmware updates patch security vulnerabilities and improve performance.
- Use a firewall:A firewall helps protect your network from unauthorized access. Most routers have built-in firewalls, but you can also install a third-party firewall on your Mac.
Protecting Against Phishing Attacks
Phishing attacks are a common tactic used by cybercriminals to steal sensitive information like usernames, passwords, and credit card details. They often disguise themselves as legitimate organizations or individuals to trick you into revealing personal information. Understanding the common tactics used in phishing scams and how to identify suspicious emails and websites can help you protect yourself from becoming a victim.
So, you want to lock down your Mac like it’s Fort Knox? The NSA has some seriously good tips for that. But hey, who needs a secure computer when you can use your iPhone’s flash to, like, totally blast a fly off the wall?
Check out this article Forget taking photos — the iPhone’s flash is way more useful than that for some seriously cool hacks. Anyways, back to your Mac, if you’re really into security, maybe you should just go full-on offline and live in a cabin in the woods.
Just saying.
Identifying Suspicious Emails
Phishing emails can be very convincing, but there are some telltale signs that you can look out for to identify them. Here are some common tactics used in phishing scams:* Urgency and Scarcity:Phishing emails often create a sense of urgency or scarcity, claiming that you need to act immediately or you’ll miss out on something important.
Imitation of Legitimate Organizations
These emails will often mimic the look and feel of legitimate organizations, using their logos, fonts, and color schemes.
Suspicious Links and Attachments
Phishing emails often contain malicious links or attachments that, when clicked, can lead to the download of malware or the theft of your personal information.
Grammatical Errors and Typos
Phishing emails may contain grammatical errors or typos, as they are often created by non-native English speakers or by automated systems.
Requests for Personal Information
Be wary of any email that asks for personal information, such as your username, password, credit card number, or Social Security number.
Identifying Suspicious Websites
Just like with emails, phishing websites can be designed to look like legitimate websites. They may even have a valid SSL certificate, which can give them a false sense of security. Here are some tips for identifying suspicious websites:* Check the URL:Look closely at the website address.
It may be misspelled or contain strange characters.
Look for Mismatched Branding
If the website doesn’t match the branding of the organization it claims to represent, it’s likely a phishing website.
Check for Security Features
Look for a lock icon in the address bar, which indicates that the website is using HTTPS encryption.
Check the Website’s Reputation
You can use a website reputation checker to see if the website has been reported as a phishing website.
Be Skeptical
If something seems too good to be true, it probably is. Be skeptical of any website that offers you something for free, especially if it asks for your personal information.
Reporting Phishing Attempts
If you think you’ve received a phishing email or visited a phishing website, it’s important to report it to the appropriate authorities. You can report phishing attempts to the Federal Trade Commission (FTC) or the Internet Crime Complaint Center (IC3).
You can also forward the phishing email to the organization that it claims to be from. By reporting phishing attempts, you can help to protect others from falling victim to these scams.
Maintaining Strong Security Habits
You’ve taken the first steps toward a more secure Mac by understanding the basics and implementing key security measures. Now, it’s time to cultivate strong security habits that will protect your system in the long run. Think of it like a healthy lifestyle for your Mac – a few simple routines can go a long way in keeping it safe and sound.
Daily Security Practices
Maintaining a secure Mac is like brushing your teeth – it’s a daily practice that keeps things healthy. Here’s a checklist of essential daily habits to incorporate:
- Keep Your Software Up-to-Date:Software updates often include security patches that fix vulnerabilities. macOS, applications, and even your web browser should be updated regularly. You can set your Mac to automatically update software, making it a hassle-free process.
- Be Wary of Email Attachments:Phishing emails can disguise malicious attachments as legitimate files. Always be cautious when opening attachments, especially from unknown senders. Hover over links to see their actual destination before clicking, and if you’re unsure, err on the side of caution and don’t open the attachment.
- Use Strong Passwords:Strong passwords are crucial for protecting your accounts. Avoid using common words or personal information, and consider using a password manager to generate and store strong passwords for you.
- Enable Two-Factor Authentication:Two-factor authentication adds an extra layer of security by requiring a code from your phone in addition to your password when logging in. This makes it much harder for unauthorized users to access your accounts.
- Be Mindful of Websites You Visit:Websites can be a source of malware. Avoid visiting suspicious websites, and always be careful about downloading files from unknown sources.
Regular System Backups
Think of regular system backups as your Mac’s safety net. They create a copy of your important data, so even if your hard drive fails or your system is compromised, you can restore your data to a previous state.
- Time Machine:macOS includes a built-in backup tool called Time Machine. It’s simple to use and automatically creates regular backups of your data to an external drive.
- Cloud Backups:Cloud backup services, like iCloud or other third-party providers, store your data in a secure data center. This can be a good option if you need to access your data from multiple devices or if you’re concerned about your local hard drive failing.
- Backup Frequency:The frequency of your backups depends on how often you change your data. For most users, daily or weekly backups are sufficient.
Staying Informed About Emerging Security Threats
The security landscape is constantly evolving, so staying informed is crucial. Here are some ways to stay up-to-date on emerging threats:
- Subscribe to Security Newsletters:Many reputable security organizations offer newsletters that provide updates on the latest threats and vulnerabilities.
- Follow Security Experts on Social Media:Security researchers and experts often share insights and updates on social media platforms like Twitter.
- Read Security Blogs:Numerous security blogs offer valuable information on emerging threats and best practices.
Understanding NSA Recommendations
The National Security Agency (NSA) provides guidance on securing Mac systems, drawing upon its expertise in cybersecurity. This guidance aims to help individuals and organizations protect their data and systems from malicious actors.
Comparison with Industry Best Practices
The NSA’s recommendations largely align with industry best practices for securing Mac systems. They emphasize the importance of strong passwords, regular software updates, and the use of anti-malware software. These recommendations are widely accepted within the cybersecurity community as crucial for maintaining a secure computing environment.
Effectiveness in Real-World Scenarios
The effectiveness of the NSA’s guidance depends on various factors, including the user’s adherence to the recommendations, the sophistication of the threats faced, and the specific configuration of the Mac system. In real-world scenarios, the NSA’s recommendations have been shown to be effective in mitigating many common threats, such as phishing attacks and malware infections.
However, emerging threats and advanced attackers may require more specialized security measures beyond the NSA’s general guidance.
Implementing Advanced Security Measures
Beyond the basics, there are more advanced security measures you can implement to further harden your Mac and protect your data. These measures go beyond the everyday practices and delve into more technical aspects, offering a higher level of protection against sophisticated threats.
Firewalls and Intrusion Detection Systems
Firewalls act as a barrier between your Mac and the outside world, scrutinizing incoming and outgoing network traffic. They block unauthorized access to your system, preventing malicious actors from infiltrating your network. Intrusion Detection Systems (IDS) go a step further by monitoring network activity for suspicious patterns, alerting you to potential threats.
While macOS includes a built-in firewall, you can further enhance your security by considering third-party firewall solutions. These offer more granular control and advanced features like intrusion prevention, allowing you to customize your security posture.
Sandboxing
Sandboxing is a security mechanism that isolates applications from your system, limiting their access to sensitive data and preventing them from causing harm. When an application runs in a sandbox, it operates in a restricted environment, unable to interact with other applications or modify system files.
This helps prevent malware from spreading or causing damage.macOS leverages sandboxing for certain applications, such as web browsers and email clients, to mitigate potential security risks. However, you can also manually configure sandboxing settings for individual applications.
Configuring Security Settings for Specific Applications
Many applications have their own security settings that you can adjust to further enhance your Mac’s protection. These settings often control access to specific data, permissions for network access, and other security-related features.For instance, you can configure your web browser to block third-party cookies, prevent websites from accessing your location, and disable JavaScript for specific sites.
Similarly, you can configure your email client to scan incoming emails for malware and block attachments from suspicious senders.
Staying Proactive and Adapting to Threats
The digital landscape is constantly evolving, with new security threats emerging regularly. Staying proactive and adapting to these threats is crucial to maintaining the security of your Mac. This means staying informed about the latest vulnerabilities, conducting regular security audits, and knowing how to respond effectively in the event of a security incident.
Staying Informed About New Security Vulnerabilities
Staying up-to-date on the latest security vulnerabilities is essential for protecting your Mac. New vulnerabilities are discovered frequently, and attackers often exploit them before patches are released. You can stay informed by following these tips:
- Subscribe to security newsletters and blogs:Many reputable security organizations and websites publish regular newsletters and blog posts that highlight new vulnerabilities and security threats. These resources can provide valuable insights into the latest threats and how to protect yourself. Examples include the SANS Institute, NIST, and the US-CERT website.
- Follow security researchers on social media:Security researchers often share their findings on Twitter and other social media platforms. Following these researchers can provide you with early warnings about new vulnerabilities and security threats. For instance, many security researchers share their findings on Twitter using the hashtag #infosec.
- Check for security updates regularly:Apple releases security updates regularly to address vulnerabilities in macOS. Ensure you install these updates as soon as they are available to patch any known vulnerabilities. You can configure your Mac to automatically install updates or manually check for them in System Preferences.
Conducting Regular Security Audits and Assessments
Regular security audits and assessments are critical for identifying vulnerabilities and weaknesses in your Mac’s security posture. These assessments can help you identify potential threats and take steps to mitigate them before they can be exploited.
- Use security scanning tools:Many security scanning tools can help identify vulnerabilities on your Mac. These tools can scan your system for malware, weak passwords, and other security risks. Examples include Malwarebytes, Intego VirusBarrier, and Sophos Home Premium.
- Perform manual checks:In addition to using security scanning tools, you can also perform manual checks to assess your Mac’s security. This includes reviewing your system’s security settings, checking for suspicious applications, and ensuring your firewall is enabled.
- Consider hiring a security professional:If you are concerned about the security of your Mac, you can consider hiring a security professional to conduct a comprehensive security audit. These professionals can identify vulnerabilities and weaknesses that you may have missed and recommend steps to improve your security posture.
Responding to Security Incidents
Despite your best efforts, you may still experience a security incident. Knowing how to respond effectively is crucial to minimizing damage and preventing future attacks.
- Identify the problem:The first step in responding to a security incident is to identify the problem. Determine what happened, when it happened, and what systems or data were affected.
- Contain the damage:Once you have identified the problem, take steps to contain the damage. This may involve disconnecting the affected system from the network, isolating the infected files, or changing passwords.
- Investigate the incident:After containing the damage, you need to investigate the incident to determine the cause and how it happened. This may involve analyzing logs, reviewing security settings, and interviewing users.
- Remediate the problem:Once you have investigated the incident, you need to remediate the problem. This may involve patching vulnerabilities, removing malware, or restoring data from backups.
- Learn from the incident:After you have remediated the problem, it is important to learn from the incident. This will help you prevent similar incidents in the future.
Conclusion
In today’s digital world, securing your Mac isn’t just about protecting your personal data; it’s about safeguarding your privacy and peace of mind. By following the steps Artikeld in this guide, you’ll be well on your way to building a robust defense against the ever-evolving threats that exist online.
Remember, security is an ongoing journey, not a destination. Stay vigilant, stay informed, and stay secure.
FAQ
What are some common vulnerabilities in Mac systems?
Mac systems can be vulnerable to various threats, including malware, phishing attacks, and unauthorized access. Common vulnerabilities include outdated software, weak passwords, and unsecured network connections.
How often should I update my macOS?
It’s crucial to keep your macOS up to date with the latest security patches. Apple releases updates regularly to address vulnerabilities and improve security. It’s recommended to install updates as soon as they become available.
Is FileVault encryption enough to protect my data?
While FileVault encryption provides a strong layer of protection, it’s not the only measure you should take. Consider using strong passwords, two-factor authentication, and a robust antivirus solution for comprehensive security.