How To Check For Pegasus Spyware On Iphone
How to check for Pegasus spyware on iPhone? This question has become increasingly relevant as the sophisticated spyware has targeted individuals across the globe. Pegasus, developed by the Israeli company NSO Group, can infiltrate iPhones and other devices, allowing attackers to access sensitive information, track location, and even control the device remotely.
The potential consequences of a Pegasus infection are serious, including financial loss, reputational damage, and even physical harm. Understanding the signs of infection, utilizing iOS security features, and employing third-party security tools are crucial steps in protecting your iPhone from this insidious threat.
This article will delve into the world of Pegasus spyware, providing a comprehensive guide to help you identify, prevent, and mitigate the risks associated with this advanced threat. We will explore the capabilities of Pegasus, its potential impacts, and the methods used to detect its presence.
Additionally, we will discuss effective strategies for safeguarding your iPhone and the crucial role of Apple in combating this threat. By understanding the intricacies of Pegasus and adopting a proactive security approach, you can significantly reduce the risk of becoming a victim of this sophisticated spyware.
Understanding Pegasus Spyware
Pegasus is a powerful and sophisticated spyware developed by the Israeli company NSO Group. It’s known for its ability to infiltrate and compromise iPhones and Android devices, granting attackers complete control over the target’s phone.
Pegasus Spyware Capabilities
Pegasus is a highly advanced spyware that can perform a wide range of actions on a compromised device. It can:
- Access and record phone calls:Pegasus can silently record phone calls and conversations, giving attackers a direct line into the victim’s private communications.
- Intercept and read messages:It can intercept and read messages from various apps, including WhatsApp, Telegram, and iMessage, allowing attackers to monitor the victim’s conversations.
- Access and steal data:Pegasus can access and steal data from the device, including contacts, photos, videos, and browsing history, giving attackers a comprehensive view of the victim’s personal and professional life.
- Track location:It can track the victim’s location in real-time, providing attackers with detailed information about their movements.
- Control the device remotely:Pegasus allows attackers to remotely control the device, enabling them to activate the camera and microphone, install and uninstall apps, and even delete data.
Potential Risks Associated with Pegasus Infection
A Pegasus infection poses significant risks to individuals and organizations, including:
- Privacy violation:The most immediate risk is the violation of privacy. Pegasus can access and steal sensitive personal information, including financial details, medical records, and personal communications.
- Financial fraud:Attackers can use stolen financial data to commit fraud, leading to financial losses for the victim.
- Reputational damage:The exposure of sensitive information can damage the victim’s reputation, both personally and professionally.
- Physical safety:Pegasus can be used to track the victim’s location, potentially putting them at risk of physical harm.
- National security threats:Pegasus has been implicated in several cases of espionage and political repression, highlighting the potential for national security threats.
Real-World Examples of Pegasus Exploitation
There have been numerous documented cases of Pegasus exploitation around the world, demonstrating its potential for harm:
- Journalists and human rights activists:In 2019, a group of journalists and human rights activists were targeted by Pegasus spyware, leading to widespread concern about the abuse of this technology.
- Political figures:Pegasus has been used to target political figures, including opposition leaders and journalists, raising concerns about its potential for political interference.
- Business executives:Pegasus has also been used to target business executives, potentially for corporate espionage and competitive advantage.
Signs of Pegasus Infection
Pegasus is a sophisticated spyware that can be challenging to detect. However, certain signs might indicate its presence on your iPhone. These signs are not always conclusive, but if you notice a combination of them, it’s crucial to take action.
Unusual Battery Drain
Pegasus can drain your iPhone’s battery significantly faster than usual. This is because the spyware constantly runs in the background, monitoring your activities and sending data to its operators. If you’ve noticed a sudden and inexplicable drop in your battery life, it might be a sign of Pegasus infection.
Data Usage Spikes
Pegasus can also lead to unusual data usage spikes. The spyware requires a constant internet connection to transmit stolen data, which can result in an increase in your mobile data usage. If you notice your data usage suddenly increasing without any apparent reason, it’s worth investigating further.
Unexpected App Behavior
Pegasus can interfere with the normal operation of your apps. You might encounter unexpected app crashes, freezes, or slow performance. The spyware might be attempting to access sensitive information or interfere with your device’s functionality.
Suspicious Apps
Pegasus can disguise itself as a legitimate app or even be installed without your knowledge. If you see unfamiliar apps on your iPhone, especially those with vague or suspicious names, it’s crucial to investigate their origins and permissions.
Unusual Network Activity
Pegasus might cause unusual network activity on your iPhone. You might notice your device connecting to unfamiliar servers or transmitting data at unusual times. If you’re not expecting these activities, it’s a potential sign of a Pegasus infection.
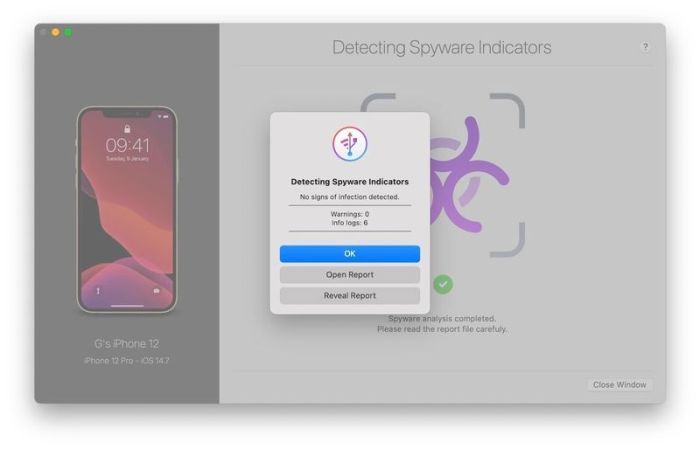
Checking for Pegasus with iOS Security Features: How To Check For Pegasus Spyware On IPhone
iOS is known for its strong security features, and Apple actively works to protect users from spyware like Pegasus. While iOS security features can’t guarantee complete protection, they offer a significant layer of defense against such threats.
If you’re worried about Pegasus spyware on your iPhone, it’s definitely worth taking a look at your security settings. But hey, if you’re looking for a break from all that tech stress, why not try plugging your guitar into your iPhone and jamming out?
How to plug your guitar into your iPhone and rock out is a great resource for that! After you’ve rocked out for a bit, you can come back to checking for Pegasus spyware, but remember, sometimes the best defense is a good offense, and a little bit of guitar shredding can really help you unwind.
Using iOS Security Features to Detect Pegasus
iOS security features provide a powerful line of defense against Pegasus and other forms of spyware. Here’s how you can utilize these features to enhance your security:
- Enable Two-Factor Authentication (2FA):2FA adds an extra layer of security by requiring a second authentication factor, typically a code sent to your phone, in addition to your password. This makes it significantly harder for attackers to gain access to your account even if they obtain your password.
- Keep Your Software Updated:Apple regularly releases software updates to address security vulnerabilities. Installing these updates promptly is crucial to protect your device from known exploits that Pegasus might use to gain access.
- Scrutinize App Permissions:When installing apps, carefully review the permissions they request. If an app asks for access to sensitive data like your contacts, microphone, or location without a clear reason, it might be suspicious.
- Use a VPN:A VPN encrypts your internet traffic, making it harder for attackers to intercept your data, including any communications that Pegasus might try to exploit.
- Be Cautious of Suspicious Links and Attachments:Avoid clicking on links or opening attachments from unknown sources, as they could contain malicious code that installs spyware like Pegasus.
Using Third-Party Security Tools
While iOS offers built-in security features, using third-party security tools can provide an extra layer of protection against Pegasus and other sophisticated threats. These tools often employ advanced detection techniques and can identify suspicious activities that might go unnoticed by standard security measures.
Reputable Third-Party Security Tools
Here are some reputable third-party security tools that can help detect Pegasus spyware on your iPhone:
- Lookout Mobile Security:Lookout Mobile Security is a comprehensive security suite that includes features for detecting and removing malware, including Pegasus. It uses advanced machine learning algorithms to analyze app behavior and identify suspicious activities. Lookout also provides real-time threat detection and alerts, notifying users of potential threats.
- Sophos Intercept X for Mobile:Sophos Intercept X for Mobile is another powerful security tool that offers robust protection against Pegasus and other mobile threats. It uses a combination of static and dynamic analysis techniques to identify malicious apps and suspicious behavior. Sophos also provides proactive threat detection and prevention features, such as anti-phishing and anti-ransomware protection.
- Kaspersky Mobile Antivirus:Kaspersky Mobile Antivirus is a popular security solution that includes features for detecting and removing Pegasus spyware. It uses advanced malware detection technologies, including behavioral analysis and signature-based detection, to identify and neutralize threats. Kaspersky also offers real-time protection against phishing attacks and other online threats.
Functionality and Detection Methods
Third-party security tools utilize a variety of methods to detect Pegasus and other spyware:
- Behavioral Analysis:These tools monitor app behavior and identify unusual patterns that could indicate malicious activity. For example, they might detect excessive data usage, unauthorized access to sensitive information, or unusual communication patterns.
- Signature-Based Detection:Some tools rely on a database of known Pegasus signatures to identify infected devices. These signatures are unique patterns or characteristics associated with the spyware.
- Sandboxing:This technique isolates suspect apps in a controlled environment to analyze their behavior without affecting the device. Sandboxing allows security tools to detect malicious activities without risking harm to the user’s data.
- Network Monitoring:Third-party tools can monitor network traffic for suspicious communication patterns that could indicate Pegasus activity. This includes identifying unusual connections to known Pegasus servers or unusual data transfer volumes.
Effectiveness Comparison
The effectiveness of different security tools can vary depending on factors such as the specific detection methods used, the sophistication of the spyware, and the user’s security practices. It’s important to choose a tool that has a proven track record of detecting Pegasus and other mobile threats.
- Independent Testing:Look for security tools that have been independently tested and certified by reputable organizations, such as AV-Test or Virus Bulletin. These organizations evaluate security tools based on their effectiveness in detecting and removing malware.
- User Reviews:Read user reviews to get insights into the real-world effectiveness of different security tools. Look for reviews from users who have encountered Pegasus or other mobile threats.
- Features and Functionality:Consider the features and functionality offered by different security tools. Choose a tool that provides a comprehensive suite of security features, including real-time protection, malware detection, and anti-phishing capabilities.
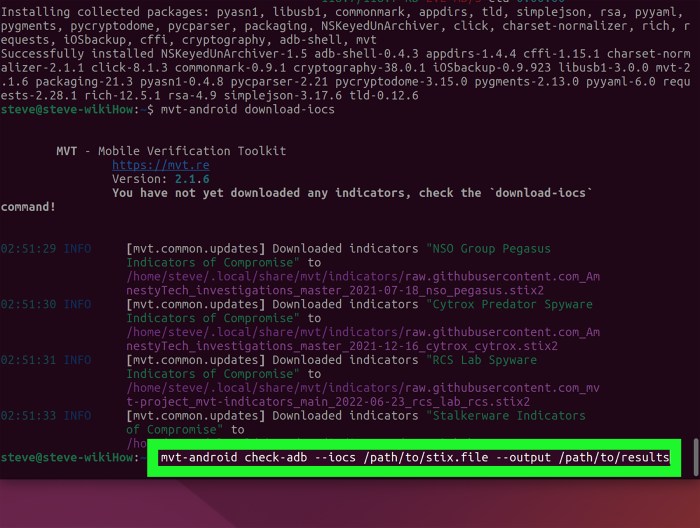
Forensic Analysis for Pegasus Detection
Forensic analysis plays a crucial role in identifying Pegasus spyware on an iPhone, offering a deeper level of investigation than standard security checks. This process involves examining the device’s data and system logs for traces of the malware’s activity, revealing its presence and potentially uncovering its actions.
Forensic Analysis Techniques
Forensic analysis for Pegasus detection utilizes specialized tools and techniques to meticulously examine the iPhone’s data and system logs. These techniques provide a comprehensive approach to identifying the malware’s presence and understanding its impact.
- Memory Analysis:This technique examines the iPhone’s RAM for any suspicious processes or code associated with Pegasus. It involves analyzing the running applications and their memory usage to detect potential signs of malware activity.
- File System Analysis:This technique involves a thorough examination of the iPhone’s file system, including directories, files, and their timestamps. By analyzing the contents and modification times of files, forensic analysts can identify potential Pegasus components or traces of its activities.
- Network Analysis:This technique focuses on analyzing the iPhone’s network traffic, examining the communication patterns and data exchange with external servers. This helps identify suspicious connections or data transfers associated with Pegasus.
- Log Analysis:Forensic analysts scrutinize the iPhone’s system logs, which record events and activities on the device. By examining these logs, they can identify unusual or suspicious entries related to Pegasus, such as unauthorized application installations, data transfers, or network connections.
Specialized Tools for Forensic Analysis
Forensic analysis relies on specialized tools to perform the complex tasks of data acquisition, analysis, and reporting. These tools provide forensic analysts with the necessary capabilities to effectively examine the iPhone’s data and identify Pegasus spyware.
- Data Acquisition Tools:These tools enable the extraction of data from the iPhone’s file system, memory, and network traffic, ensuring a complete and accurate data set for analysis.
- Analysis Tools:Forensic analysts utilize analysis tools to process and examine the acquired data, looking for patterns, anomalies, and suspicious activities associated with Pegasus.
- Reporting Tools:These tools facilitate the creation of comprehensive reports documenting the findings of the forensic analysis, outlining the evidence of Pegasus infection and its potential impact on the iPhone.
Limitations and Challenges of Forensic Analysis, How to check for Pegasus spyware on iPhone
While forensic analysis offers a powerful approach to detecting Pegasus spyware, it faces certain limitations and challenges.
- Data Availability:The success of forensic analysis depends on the availability of relevant data. If the iPhone has been compromised for an extended period, critical data may have been deleted or overwritten, hindering the investigation.
- Complexity of Analysis:Analyzing the iPhone’s data and logs requires specialized expertise and knowledge of forensic techniques. The complexity of the analysis can make it time-consuming and challenging, especially for less experienced analysts.
- Evolving Malware:Pegasus spyware is constantly evolving, with attackers employing new techniques and obfuscation methods to evade detection. This requires forensic analysts to stay updated on the latest malware tactics and adapt their analysis accordingly.
Protecting Against Pegasus Infection
Pegasus is a powerful spyware capable of infiltrating iPhones, potentially giving attackers access to sensitive information and even control over your device. While Apple has implemented robust security measures, it’s crucial to take proactive steps to protect your iPhone from Pegasus attacks.
This section delves into the key strategies for safeguarding your iPhone from Pegasus infection. By following these recommendations, you can significantly reduce the risk of falling victim to this sophisticated spyware.
So, you’re worried about Pegasus spyware on your iPhone? That’s totally understandable. While you’re figuring out how to check, maybe you can take a break and Update your Brydge keyboard for multitouch support on iPad – it’ll make typing a lot smoother! Once you’re done with that, you can get back to checking for Pegasus.
Just remember, keeping your devices secure is always a good idea!
Implementing a Comprehensive Security Strategy
A robust security strategy involves a combination of proactive measures, including:
- Keeping your iOS updated:Apple regularly releases security updates to patch vulnerabilities that could be exploited by Pegasus. Ensuring your iPhone is running the latest iOS version is paramount to staying protected.
- Using strong passcodes:A strong passcode, preferably a combination of letters, numbers, and symbols, acts as a crucial barrier against unauthorized access. Avoid using common or easily guessable passcodes.
- Enabling Two-Factor Authentication (2FA):2FA adds an extra layer of security by requiring a second verification code, typically sent to your trusted device, in addition to your password. This significantly reduces the risk of unauthorized access, even if your password is compromised.
- Being cautious about suspicious links and attachments:Pegasus can be delivered through malicious links or attachments in emails, text messages, or social media messages. Always exercise caution before clicking on suspicious links or opening attachments from unknown senders.
- Downloading apps only from trusted sources:The App Store is Apple’s official app marketplace and a generally safe source for downloading apps. Avoid downloading apps from third-party sources, as they could contain malware.
- Regularly checking for suspicious activity:Keep an eye out for unusual activity on your iPhone, such as unexpected data usage, battery drain, or apps you don’t recognize. These could be signs of a Pegasus infection.
Best Practices for Secure iPhone Usage
Following these best practices can further enhance your iPhone’s security and minimize the risk of Pegasus infection:
- Limit app permissions:When installing an app, carefully review the permissions it requests. Grant only the permissions necessary for the app’s functionality. Avoid granting access to sensitive data like contacts, location, or microphone unless absolutely required.
- Be mindful of your location data:Pegasus can use location data to track your movements. Consider limiting location access for apps that don’t need it. Use the “Precise Location” setting cautiously, as it provides more detailed location information.
- Use a VPN:A Virtual Private Network (VPN) encrypts your internet traffic, making it more difficult for attackers to intercept your data, including your location information.
- Avoid using public Wi-Fi networks:Public Wi-Fi networks are often unsecured, making them vulnerable to attacks. If you must use public Wi-Fi, use a VPN for added security.
- Regularly backup your data:Back up your iPhone regularly to iCloud or your computer. This ensures you can restore your data in case of a Pegasus infection or other device issues.
- Consider using a security app:Some third-party security apps can help detect and remove malware, including Pegasus. However, choose reputable security apps from trusted developers.
Reporting Pegasus Suspicion
If you suspect your iPhone has been infected with Pegasus spyware, it’s crucial to take action to protect yourself and potentially prevent further intrusion. Reporting your suspicion to the appropriate authorities is an essential step in this process.
Reporting Channels and Resources
Reporting a suspected Pegasus infection involves contacting relevant authorities and organizations. These entities are equipped to investigate your claim and provide guidance on mitigating the threat.
- National Cyber Security Agencies:Contact your country’s national cyber security agency, which often has specialized units dedicated to investigating spyware and cyberattacks. For instance, in the United States, you can reach out to the Cybersecurity and Infrastructure Security Agency (CISA).
- Law Enforcement Agencies:If you believe your personal information or privacy has been compromised, you can report the incident to your local law enforcement agency. They can investigate the matter and potentially pursue legal action against the perpetrators.
- Privacy Advocacy Organizations:Organizations like the Electronic Frontier Foundation (EFF) and Privacy International provide resources and support for individuals concerned about spyware and privacy violations. They can offer guidance on reporting your concerns and navigating the legal complexities involved.
- Journalists and Researchers:If you have evidence of a Pegasus infection and believe it’s part of a larger pattern of surveillance, you can consider contacting investigative journalists or researchers specializing in cybersecurity and spyware. They may be able to shed light on the broader context of your case and raise awareness about the issue.
Steps Involved in Reporting
When reporting a suspected Pegasus infection, it’s helpful to gather as much information as possible to strengthen your case and aid the investigation.
- Document the Evidence:Keep detailed records of any suspicious activity on your iPhone, including unusual battery drain, unexpected data usage, or any unusual apps or permissions granted. Screenshots, logs, and timestamps can be valuable evidence.
- Preserve the Device:If possible, avoid using your iPhone extensively until you’ve reported the suspicion. This can help prevent further data compromise and preserve potential evidence.
- Contact the Appropriate Authority:Use the reporting channels mentioned above to contact the relevant authority. Clearly explain your concerns and provide as much information as you have.
- Follow Up:After reporting, keep track of the investigation’s progress and any follow-up actions you need to take.
The Role of Apple in Pegasus Mitigation
Apple has been actively involved in the fight against Pegasus and other spyware, recognizing the importance of user privacy and security. The company has implemented various measures to protect its users from these threats, demonstrating a commitment to safeguarding user data and enhancing the overall security of its ecosystem.
Apple’s Efforts in Combating Pegasus
Apple has taken a proactive stance in combating Pegasus and other spyware, demonstrating its commitment to user privacy and security. The company has implemented several measures to protect its users from these threats, including:
- Strengthening iOS Security: Apple has continuously enhanced the security of iOS, its mobile operating system, to make it more resistant to spyware attacks. These efforts include implementing stronger encryption, sandboxing applications, and introducing features like “App Transparency Tracking” to limit the ability of apps to track user activity.
- Issuing Security Updates: Apple regularly releases security updates to address vulnerabilities that could be exploited by spyware. These updates patch security flaws and improve the overall security posture of iOS devices, making it harder for attackers to gain unauthorized access.
- Collaboration with Security Researchers: Apple collaborates with security researchers to identify and address vulnerabilities in its products. This collaboration helps improve the security of iOS and other Apple devices, making them more resistant to spyware attacks.
- Publicly Condemning Pegasus: Apple has publicly condemned the use of Pegasus and other spyware, emphasizing its commitment to protecting user privacy and security. The company has also taken legal action against companies involved in developing and selling spyware.
Apple’s Mechanisms for Protecting User Privacy
Apple has implemented various mechanisms to protect user privacy and security, making it more difficult for spyware like Pegasus to operate effectively. These mechanisms include:
- End-to-End Encryption: Apple uses end-to-end encryption for various services, including iMessage and FaceTime, ensuring that only the sender and receiver can access the content of communications. This prevents third parties, including spyware, from intercepting or monitoring user data.
- Differential Privacy: Apple utilizes differential privacy in its data collection practices, adding noise to user data before it is analyzed. This makes it difficult for attackers to extract sensitive information from aggregated data sets, protecting user privacy.
- Privacy-Focused Features: Apple has introduced several privacy-focused features in iOS, such as “App Transparency Tracking,” which allows users to control which apps can track their activity. These features empower users to manage their privacy and limit the amount of data shared with apps and third parties.
Effectiveness of Apple’s Security Measures
While Apple’s efforts have significantly improved the security of its ecosystem, Pegasus and other spyware continue to pose a threat.
- Zero-Day Exploits: Attackers may exploit zero-day vulnerabilities, previously unknown flaws in software, to gain access to devices before Apple can issue a patch. These vulnerabilities can be difficult to detect and address, making it challenging for Apple to completely prevent spyware infections.
- Social Engineering: Attackers can use social engineering techniques to trick users into installing malicious software or providing access to their devices. These techniques can bypass even the most robust security measures, making user education and awareness crucial.
- Targeted Attacks: Pegasus and other spyware are often used in targeted attacks against individuals of interest. These attacks may involve sophisticated techniques that can bypass standard security measures, requiring specialized defenses and vigilance.
Future Trends in Spyware Detection
The landscape of spyware threats is constantly evolving, prompting a need for innovative detection and mitigation strategies. New technologies and approaches are emerging to counter these sophisticated threats, pushing the boundaries of security.
The Rise of AI-Powered Detection
AI and machine learning are playing an increasingly crucial role in spyware detection. These technologies can analyze vast amounts of data to identify patterns and anomalies indicative of spyware activity. AI-powered solutions can:* Detect unusual network traffic:AI algorithms can identify suspicious communication patterns that might indicate spyware attempting to exfiltrate data.
Analyze system behavior
AI can monitor system performance, application usage, and file access patterns to detect changes that could be linked to spyware installation or operation.
Identify malicious code
AI can analyze code for potential indicators of malicious intent, even if the code is obfuscated or disguised.
Checking for Pegasus spyware on your iPhone can feel like a daunting task, but it’s worth the effort to protect your privacy. While there are specific steps you can take to detect Pegasus, keeping your iPhone updated with the latest iOS version is crucial.
This includes making sure your HomePod is up-to-date, which you can learn how to do here. Once your devices are running the latest software, you’ll have the most recent security patches, making it harder for any spyware to infiltrate your systems.
The Evolution of Mobile Security
Mobile devices are becoming increasingly vulnerable to spyware attacks. As a result, mobile security solutions are evolving to address these threats:* Enhanced sandboxing:Mobile operating systems are incorporating more robust sandboxing mechanisms to isolate applications and prevent them from accessing sensitive data.
Real-time threat detection
Antivirus and anti-malware software are incorporating real-time threat detection capabilities to identify and neutralize spyware as soon as it attempts to infiltrate a device.
Privacy-focused security solutions
Privacy-focused security solutions are emerging to protect users’ data from unauthorized access and surveillance, including spyware.
The Importance of Proactive Security
Proactive security measures are becoming increasingly important in the fight against spyware. These measures aim to prevent spyware infections in the first place:* Regular security updates:Users should ensure their devices are running the latest security updates to patch vulnerabilities that could be exploited by spyware.
App vetting
Users should be cautious about downloading and installing apps from unknown sources, as these apps could potentially contain spyware.
Privacy settings
Users should carefully review and configure their privacy settings to limit the amount of personal data they share with apps and services.
Closing Notes
Protecting your iPhone from Pegasus spyware requires a multi-faceted approach that includes staying informed, utilizing security features, and employing third-party tools. While no system is completely immune to sophisticated threats, taking proactive steps can significantly reduce your vulnerability. Remember, staying vigilant and informed about emerging threats is essential in maintaining the security and privacy of your digital life.
By implementing the strategies Artikeld in this article, you can empower yourself to combat the growing threat of Pegasus and other forms of spyware.
Clarifying Questions
Is Pegasus spyware only a threat to iPhones?
No, Pegasus can target various operating systems, including Android, Windows, and macOS. However, iPhones have been a particular focus due to their robust security measures.
How do I know if my iPhone is infected with Pegasus?
Identifying a Pegasus infection can be challenging, as the spyware is designed to operate stealthily. However, some indicators include unusual battery drain, increased data usage, unexpected app behavior, and suspicious network activity.
What should I do if I suspect my iPhone is infected with Pegasus?
If you suspect your iPhone is infected, contact a reputable security professional or forensic analyst for assistance. They can conduct a thorough investigation and provide guidance on appropriate actions.
Are there any free tools to detect Pegasus spyware?
While some free tools may claim to detect Pegasus, they are often less reliable than paid professional solutions. For comprehensive detection, consider using reputable third-party security tools.