Configure Firewall Settings To Protect Your Pc From Unauthorized Access
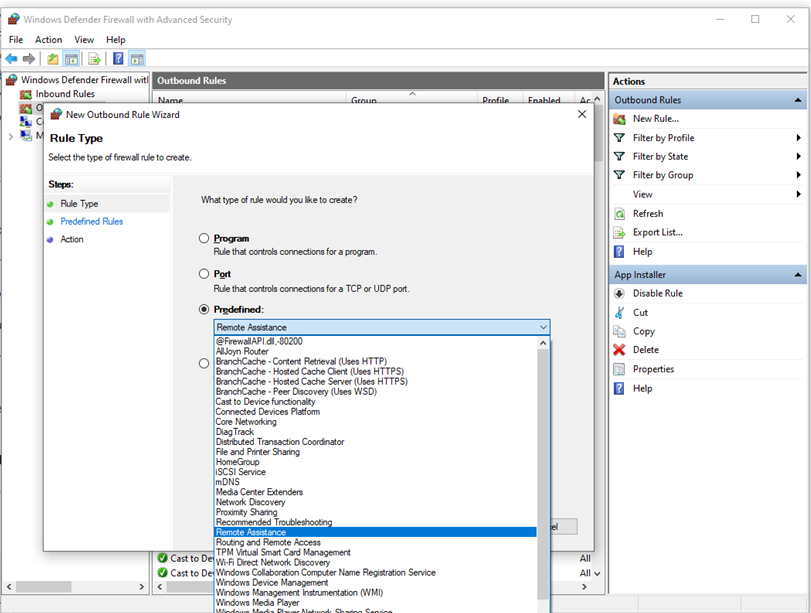
Configure Firewall Settings to Protect Your PC from Unauthorized Access is the process of adjusting firewall settings to prevent unauthorized individuals from accessing your computer through a network. For example, you can configure your firewall to block incoming connections from specific IP addresses or ports, or to only allow connections from trusted sources.
Configuring firewall settings is important because it helps to protect your computer from malware, hackers, and other threats. By blocking unauthorized access, you can help to keep your personal information and data safe. One key historical development in firewall technology was the introduction of stateful firewalls in the 1990s. Stateful firewalls track the state of network connections and can more effectively block unauthorized access than traditional firewalls.
This article will provide a step-by-step guide on how to configure firewall settings on your PC. We will also discuss the different types of firewall settings and how to choose the best settings for your needs.
Configure Firewall Settings to Protect Your PC from Unauthorized Access
Configuring firewall settings is essential to protect your PC from unauthorized access. A firewall is a network security system that monitors and controls incoming and outgoing network traffic. By configuring your firewall settings, you can prevent unauthorized users from accessing your computer through a network connection.
- Block unauthorized access
- Prevent malware and viruses
- Protect personal information
- Secure online transactions
- Control network traffic
- Monitor network activity
- Log security events
- Enforce security policies
- Receive security updates
- Configure advanced security settings
Configuring your firewall settings is a critical part of protecting your PC from online threats. By understanding the different aspects of firewall settings, you can configure your firewall to meet your specific security needs.
Block unauthorized access
Blocking unauthorized access is a critical aspect of protecting your PC from online threats. By configuring your firewall settings to block unauthorized access, you can prevent hackers and other malicious actors from accessing your computer and stealing your personal information, corrupting your files, or launching attacks on other computers.
-
IP filtering
IP filtering allows you to block access to your computer from specific IP addresses. This is useful for blocking known malicious IP addresses or IP addresses from countries that you do not visit. -
Port filtering
Port filtering allows you to block access to specific ports on your computer. This is useful for blocking access to ports that are commonly used by hackers to attack computers. -
Application filtering
Application filtering allows you to block access to specific applications on your computer. This is useful for blocking applications that are known to be vulnerable to attack or that you do not want to allow access to the network. -
Stateful inspection
Stateful inspection is a more advanced firewall feature that tracks the state of network connections and can more effectively block unauthorized access. Stateful inspection firewalls can detect and block attacks that traditional firewalls cannot.
By configuring your firewall settings to block unauthorized access, you can significantly reduce the risk of your computer being attacked. Firewall settings are an essential part of a comprehensive security strategy, and they should be configured properly to protect your computer from online threats.
Prevent malware and viruses
Preventing malware and viruses is a critical aspect of protecting your PC from unauthorized access. Malware and viruses are malicious software programs that can damage your computer, steal your personal information, or launch attacks on other computers. By configuring your firewall settings to prevent malware and viruses, you can significantly reduce the risk of your computer being infected.
-
Block malicious websites
Firewall settings can be used to block access to known malicious websites. This is an effective way to prevent malware and viruses from being downloaded onto your computer. -
Block malicious IP addresses
Firewall settings can also be used to block access to known malicious IP addresses. This is an effective way to prevent malware and viruses from being downloaded onto your computer from specific sources. -
Block malicious email attachments
Firewall settings can also be used to block access to malicious email attachments. This is an effective way to prevent malware and viruses from being downloaded onto your computer via email. -
Block malicious software downloads
Firewall settings can also be used to block access to malicious software downloads. This is an effective way to prevent malware and viruses from being downloaded onto your computer from the internet.
By configuring your firewall settings to prevent malware and viruses, you can significantly reduce the risk of your computer being infected. Firewall settings are an essential part of a comprehensive security strategy, and they should be configured properly to protect your computer from online threats.
Protect personal information
Configuring firewall settings to protect your PC from unauthorized access is critical for protecting your personal information. Unauthorized access to your computer can give criminals access to your personal files, financial information, and other sensitive data. By configuring your firewall settings properly, you can prevent unauthorized users from accessing your computer and stealing your personal information.
There are a number of ways that you can configure your firewall settings to protect your personal information. One important step is to block access to known malicious websites and IP addresses. You can also block access to certain types of files, such as executable files (.exe) and compressed files (.zip). Additionally, you can configure your firewall to only allow access to specific programs and applications.
Protecting your personal information is a critical component of configuring firewall settings to protect your PC from unauthorized access. By taking the steps to protect your personal information, you can help to keep your computer safe from online threats.
Secure online transactions
Securing online transactions is a critical aspect of configuring firewall settings to protect your PC from unauthorized access. By configuring your firewall settings properly, you can prevent unauthorized users from accessing your computer and stealing your financial information or other sensitive data.
-
Encryption
Encryption is the process of converting data into a form that cannot be easily understood by unauthorized people. When you make an online transaction, your financial information is encrypted so that it cannot be intercepted and stolen by hackers. -
Authentication
Authentication is the process of verifying that a user is who they claim to be. When you make an online transaction, you are typically required to provide your username and password. This information is used to authenticate you and ensure that you are authorized to make the transaction. -
Authorization
Authorization is the process of giving a user permission to perform a specific action. When you make an online transaction, your bank or credit card company will authorize the transaction. This ensures that you have the funds available to complete the transaction and that the transaction is not fraudulent. -
Firewalls
Firewalls are network security systems that monitor and control incoming and outgoing network traffic. By configuring your firewall settings properly, you can prevent unauthorized users from accessing your computer and stealing your financial information.
By configuring your firewall settings to secure online transactions, you can help to protect your financial information and other sensitive data. Firewall settings are an essential part of a comprehensive security strategy, and they should be configured properly to protect your computer from online threats.
Control network traffic
Controlling network traffic is a critical aspect of configuring firewall settings to protect your PC from unauthorized access. By controlling network traffic, you can prevent unauthorized users from accessing your computer and stealing your personal information, corrupting your files, or launching attacks on other computers.
-
Inbound traffic filtering
Inbound traffic filtering allows you to control which incoming network traffic is allowed to reach your computer. You can use inbound traffic filtering to block traffic from specific IP addresses, ports, or countries. -
Outbound traffic filtering
Outbound traffic filtering allows you to control which outgoing network traffic is allowed to leave your computer. You can use outbound traffic filtering to block traffic to specific IP addresses, ports, or countries. -
Port management
Port management allows you to control which ports on your computer are open to network traffic. You can use port management to close unused ports and prevent unauthorized users from accessing your computer through open ports. -
Traffic logging
Traffic logging allows you to monitor network traffic to and from your computer. You can use traffic logging to identify suspicious activity and troubleshoot network problems.
By controlling network traffic, you can significantly reduce the risk of your computer being attacked. Firewall settings are an essential part of a comprehensive security strategy, and they should be configured properly to protect your computer from online threats.
Monitor network activity
Monitoring network activity is an essential aspect of configuring firewall settings to protect your PC from unauthorized access. By monitoring network activity, you can identify suspicious activity and troubleshoot network problems.
-
Network traffic logs
Network traffic logs record all incoming and outgoing network traffic to and from your computer. You can use network traffic logs to identify suspicious activity, such as unauthorized access attempts or malware infections. -
Security alerts
Security alerts are notifications that are generated by your firewall when it detects suspicious activity. You can use security alerts to identify potential threats and take appropriate action. -
Real-time monitoring
Real-time monitoring allows you to monitor network activity in real time. This can be useful for identifying and troubleshooting network problems. -
Traffic analysis
Traffic analysis tools can help you to analyze network traffic and identify patterns and trends. This information can be used to improve your firewall settings and protect your computer from unauthorized access.
Monitoring network activity is an essential part of a comprehensive security strategy. By monitoring network activity, you can identify suspicious activity, troubleshoot network problems, and protect your computer from unauthorized access.
Log security events
Logging security events is a critical component of configuring firewall settings to protect your PC from unauthorized access. By logging security events, you can track and monitor all activity on your computer, including failed login attempts, successful logins, and other security-related events.
Security event logs can be used to identify suspicious activity, troubleshoot security problems, and provide evidence in the event of a security breach. For example, if you see multiple failed login attempts from the same IP address, this could be an indication that someone is trying to hack into your computer.
There are a number of different ways to log security events. One common method is to use the Windows Event Viewer. The Event Viewer is a built-in tool that allows you to view and manage all security events on your computer.
Another option is to use a third-party security logging tool. These tools typically provide more advanced features than the Event Viewer, such as the ability to filter and search security events, and to generate reports.
No matter which method you choose, logging security events is an essential part of configuring firewall settings to protect your PC from unauthorized access.
Enforce security policies
Enforcing security policies is a critical aspect of configuring firewall settings to protect your PC from unauthorized access. Security policies define the rules that govern how your firewall operates, and they can be used to control a wide range of security settings, including which ports are open, which types of traffic are allowed, and how unauthorized access attempts are handled.
-
Access control
Access control policies define who is allowed to access your computer and what resources they are allowed to access. This can be used to prevent unauthorized users from accessing sensitive data or making changes to your system. -
Logging and monitoring
Logging and monitoring policies define how security events are logged and monitored. This information can be used to identify and investigate security breaches, and to improve the security of your system. -
Intrusion detection and prevention
Intrusion detection and prevention policies define how your firewall detects and responds to intrusion attempts. This can include blocking suspicious traffic, generating alerts, or taking other actions to protect your system. -
Security updates
Security updates policies define how your firewall is updated with the latest security patches. This is critical for keeping your system protected from the latest threats.
By enforcing security policies, you can significantly reduce the risk of your computer being compromised by unauthorized access. Firewall settings are an essential part of a comprehensive security strategy, and they should be configured properly to protect your computer from online threats.
Receive security updates
Within the scope of “configure firewall settings to protect your PC from unauthorized access”, receiving security updates plays a crucial role in maintaining the effectiveness of your firewall and safeguarding your system against evolving threats.
-
Automatic Updates
Enabling automatic updates ensures that your firewall is always up-to-date with the latest security patches and enhancements. This eliminates the risk of vulnerabilities being exploited by attackers. -
Regular Scans
Regularly scheduled scans detect and install any available security updates for your firewall. This proactive approach helps identify and address potential weaknesses before they can be exploited. -
Threat Intelligence
Security updates often incorporate threat intelligence gathered from various sources, such as security researchers and incident response teams. By incorporating this intelligence, your firewall can better identify and block emerging threats. -
Compatibility and Stability
Security updates not only address vulnerabilities but also enhance the overall compatibility and stability of your firewall. This ensures that your firewall operates seamlessly with other security measures and your operating system.
By ensuring that your firewall receives regular security updates, you can significantly enhance its ability to protect your PC from unauthorized access and maintain a robust security posture against evolving cyber threats.
Configure advanced security settings
Within the realm of “configure firewall settings to protect your PC from unauthorized access”, configuring advanced security settings plays a vital role in strengthening your firewall’s defenses against sophisticated threats. These settings provide granular control over various aspects of your firewall, allowing you to tailor its behavior to meet your specific security requirements.
-
Intrusion Prevention System (IPS)
An IPS monitors network traffic for suspicious patterns and actively blocks malicious attempts to exploit vulnerabilities. It complements the firewall’s basic packet filtering capabilities, providing an additional layer of protection against advanced attacks.
-
Packet Inspection
Packet inspection examines the content of network packets, rather than just their headers. This enables the firewall to detect and block complex attacks that evade traditional signature-based detection methods, such as malware payloads hidden within encrypted traffic.
-
Network Address Translation (NAT)
NAT translates private IP addresses used within your network to a single public IP address facing the internet. This helps conceal the internal network structure from external attackers, reducing the attack surface and making it more difficult for unauthorized access.
-
Virtual Private Network (VPN)
A VPN encrypts all network traffic between your computer and a remote server, creating a secure tunnel through the public internet. This protects sensitive data from eavesdropping and unauthorized access, especially when using public Wi-Fi networks.
By configuring advanced security settings, you can significantly enhance the effectiveness of your firewall in safeguarding your PC from unauthorized access. These settings provide comprehensive protection against a wide range of threats, enabling you to maintain a robust security posture in the face of evolving cyber risks.
FAQs on Configuring Firewall Settings to Protect Your PC from Unauthorized Access
This section provides answers to frequently asked questions (FAQs) related to configuring firewall settings for enhanced PC security against unauthorized access. These FAQs address common concerns, provide clarifications, and offer additional insights into the subject matter.
Question 1: What is the primary purpose of a firewall?
A firewall is a network security system that monitors and controls incoming and outgoing network traffic based on predetermined security rules. Its main purpose is to prevent unauthorized access to a computer or network, thereby protecting against malicious attacks and data breaches.
Question 2: Why is it important to configure firewall settings?
Properly configured firewall settings play a critical role in maintaining PC security by blocking unauthorized access attempts, preventing malware and viruses from infiltrating the system, protecting personal information and sensitive data, and securing online transactions.
Question 3: What are some essential firewall settings to consider?
When configuring firewall settings, it’s important to focus on controlling network traffic, monitoring network activity, logging security events, enforcing security policies, receiving regular security updates, and configuring advanced security settings like intrusion prevention, packet inspection, and virtual private networks (VPNs).
Question 4: How can I configure firewall settings if I’m not a technical expert?
Most operating systems provide user-friendly interfaces for configuring firewall settings, making it accessible even for non-technical users. Additionally, various online resources, tutorials, and support forums can assist in understanding and implementing appropriate firewall configurations.
Question 5: How often should I review and update firewall settings?
Firewall settings should be reviewed and updated regularly, especially after installing new software or making changes to the network configuration. Regularly checking for and installing security updates is crucial to ensure the firewall remains effective against emerging threats and vulnerabilities.
Question 6: Are there any additional tips for enhancing firewall protection?
In addition to configuring firewall settings, implementing other security measures such as using strong passwords, keeping software up-to-date, being cautious when opening email attachments or clicking links, and using reputable antivirus and anti-malware software can further enhance the protection of your PC from unauthorized access.
Understanding and configuring firewall settings effectively is a fundamental aspect of maintaining a robust PC security posture. By addressing these FAQs, we hope to provide a clearer understanding of the importance, key considerations, and practical steps involved in optimizing firewall settings to protect against unauthorized access.
In the next section, we will delve deeper into the advanced aspects of firewall configuration, including customizing firewall rules, creating firewall zones, and implementing additional security measures to further enhance PC protection.
Tips to Configure Firewall Settings for Enhanced PC Protection
To further enhance the protection of your PC from unauthorized access, consider implementing the following tips when configuring firewall settings:
Tip 1: Customize Firewall Rules
Define specific rules to allow or block network traffic based on criteria such as IP addresses, ports, and protocols. This granular control provides more flexibility and protection.
Tip 2: Create Firewall Zones
Categorize network connections into different zones (e.g., trusted, untrusted) and apply appropriate security policies to each zone, enhancing protection based on the level of trust.
Tip 3: Enable Intrusion Prevention
Utilize an intrusion prevention system (IPS) to actively monitor and block malicious traffic, providing an additional layer of defense against sophisticated attacks.
Tip 4: Implement Two-Factor Authentication
Require additional authentication factors, such as a code sent to your mobile device, when accessing sensitive resources or making changes to firewall settings, adding an extra layer of security.
Tip 5: Regularly Update Firewall Software
Keep the firewall software up-to-date with the latest security patches and enhancements to ensure it remains effective against evolving threats and vulnerabilities.
Tip 6: Use Reputable Antivirus and Anti-Malware Software
Complement firewall protection with reputable antivirus and anti-malware software to detect and remove malicious software that may bypass the firewall.
Tip 7: Restrict Access to Sensitive Ports
Identify and restrict access to sensitive ports, such as those used for remote administration or file sharing, to minimize the risk of unauthorized access and exploitation.
Tip 8: Disable Unused Services
Disable or remove any unnecessary services or programs that may create vulnerabilities or provide entry points for attackers.
By implementing these tips, you can significantly enhance the security of your PC by configuring firewall settings effectively. These measures provide a comprehensive approach to safeguarding your system against unauthorized access and online threats.
In the final section of this article, we will discuss advanced firewall management techniques and best practices for maintaining a robust security posture.
Conclusion
Effectively configuring firewall settings is paramount in safeguarding your PC from unauthorized access and online threats. This article has explored the various aspects of firewall configuration, emphasizing the importance of controlling network traffic, monitoring activity, logging events, enforcing policies, and receiving regular security updates.
Key points to consider include:
- Customizing firewall rules and creating firewall zones provide granular control over network access.
- Advanced security measures such as intrusion prevention and two-factor authentication enhance protection against sophisticated attacks.
- Regular updates, reputable security software, and restricting access to sensitive ports further strengthen your security posture.
Remember, firewall configuration is an ongoing process that requires attention to detail and a proactive approach to security. By implementing the recommendations outlined in this article, you can significantly reduce the risk of unauthorized access and maintain a robust security posture for your PC.